2015 May 9 at the Victory Parade in Moscow, the public was first shown the latest Russian tank T-14 "Armata". The creators position it as a next-generation combat vehicle, equipped with the latest electronics, sophisticated defense and attack systems. Representatives of the Russian military industrial complex proudly stated that the Armata is a tank created in accordance with the concept of a network-centric warfare, capable of performing not only percussion functions, but also conducting reconnaissance and target designation for SAU and MRLs.
Such statements sparked interest in the term "network-centric warfare." What does he mean? Why is it called the military doctrine of the XXI century? And how ready is the Russian army for its practical use?
The network-centric war (not to be confused with the network) is a military doctrine (or concept) that was developed and first applied in practice by the Americans. It is based on the postulate that it is possible to significantly increase the effectiveness of our own troops by combining them into a single information network operating in real time. It sounds quite simple, but it took the Americans a few years, dozens of experiments and simulations, as well as hundreds of millions of dollars spent on new equipment, software, and training, to translate this idea into reality. Currently, the concept of "network-centric war" occupies an important place in the American military doctrines of Joint Vision 2010 and Joint Vision 2020.
Creating a unified information network can increase the power of the armed forces several times without increasing their numbers. The network-centric war allows you to rise to a new level of command and control, significantly reducing decision-making time. The use of new information technologies makes it possible to change the classic balance of forces between the attacking and the defending side to the opposite. Naturally, this is true under the condition that the defending side is not able to wage a network-centric war.

Net Centrism - War for the Postmodern
According to the theory of network-centric war, a huge amount of material has been written. This topic is of great interest, not only among professional military men, but also among representatives of strictly peaceful areas of knowledge.
It is believed that the history of mankind can be divided into three major phases: agrarian, industrial and post-industrial. They correspond to such sociological concepts as pre-modern, modern and post-modern. Today, the developed world lives in the postmodern era, with this period the information age is inextricably linked, which began several decades ago.
The postmodern and information age is rapidly and radically changing the way of life of humanity. A network-centric war is simply a transfer of the basic approaches and principles of the postmodern into the military sphere.
It is not surprising that the application of the network principles of postmodernism in military affairs can lead to a real revolution. This has already happened: the introduction of information and network technologies into business and the economy showed their considerable superiority over the old industrial models.
The development of military art and the change of paradigms of warfare throughout the history of mankind was determined by the range of the enemy's defeat and the number of enemies that can be destroyed in a specific unit of time. At first there were edged weapons, a bow and spears, then imperfect firearms and the first artillery samples. Then came the automatic firearms, long-range artillery, aircraft and rocket weapons. That is, at first the outcome of military conflicts was determined by means of individual destruction, then by group, today we have weapons of mass destruction.
Military equipment developed by improving combat platforms, increasing their firepower and security. The technologies of recent decades have allowed us to create truly powerful and deadly samples of military equipment. The way of managing troops has changed much less: just like hundreds of years ago, it has a clear hierarchical structure, although the speed of data transmission and processing, of course, has increased significantly.
However, it is no longer suitable for controlling modern combat platforms. Moreover, he often negates the potential capabilities of military equipment.
If we compare the doctrine of the network-centric war with the concept of Blitzkrieg (von Schlieffen, 1905) and deep operation (Triandafillov, 1931), it becomes obvious that Network-centric warfare is more flexible and provides greater efficiency in the conduct of hostilities. In traditional doctrines, all information is collected and transmitted up to headquarters, where it is processed and descended in the form of orders. The reaction rate of such a system depends on the bandwidth of the communication channels and the speed of the command work. The control is completely centralized; when a headquarters or communication channel is destroyed, such a system completely “freezes”.

Principles of network-centric warfare, its main features
The concept of a “network-centric war” was developed by three US military: Vice-Admiral Arthur Sebrovsky, Pentagon Researcher John Garstka, and Admiral Jay Johnson. It was first described in an article published in 1998.
The basis of the new concept was the assertion that it is possible to achieve victory over the enemy by achieving information and communication superiority by combining your military forces into a single network.
This makes it possible to significantly improve the quality of command and control of troops, significantly increase the pace of operations and the effectiveness of fire damage. Also, according to the developers of the doctrine, the unification of the armed forces into a single information network will significantly increase their survivability, the level of self-synchronization, and will help optimize the supply of the group.
Admiral Jay Johnson believed that the creation of a universal military information network capable of acting in real time would significantly increase the speed of command of the troops, which is ensured by a decrease in decision-making time by the command and an increase in the speed of their transfer to the troops.
A network-centric war cannot be called a new type of war; rather, it is a revolutionary way of organizing and conducting combat operations.
Due to the availability of complete information about the forces and location of the enemy, as well as the current configuration of its own troops, the command is able to preempt the enemy at all stages of deployment and combat operations.
The adversary will always be several steps behind, which will make it impossible for her to take any kind of response, which will ultimately lead to complete chaos and loss of combat capability. These theoretical calculations were fully confirmed during the course of the American military operation in Iraq (2003).
The article introduced the concept of "network-centric forces", which meant troops, weapons and military equipment capable of taking part in Network-centric warfare.
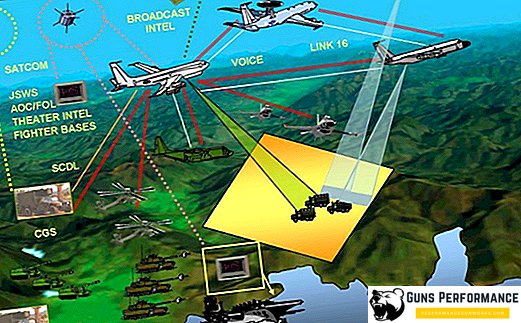
The concept of "network-centric warfare" is based on the latest scientific advances in computer and communication technology and electronics. Data channels transmit data in the form of digital and voice messages, streaming video.
The basis of the information network of network-centric warfare is GIG or the “Global Information Grid”, the operation of which is provided by a powerful grouping of navigation, reconnaissance and communication satellites. The information and communication network consists of three main elements:
- intelligence;
- governing bodies;
- means of destruction (suppression).
The theory of network-centric warfare is based on three main tenets:
- If you combine the armed forces with powerful and reliable networks, this will allow you to move to a qualitatively new level of information exchange. During network-centric combat operations, the command may receive information from individual combat vehicles and military personnel about their current location, condition and needs. No less complete is the information about the enemy, which comes directly from a variety of sources: numerous drones, space satellites, ground and electronic intelligence. In addition, users of information are also its suppliers.
- The constant exchange of information enhances its quality and the level of general awareness of the processes taking place in the theater of operations. The so-called shared awareness is achieved. A picture of a real battle taking place in the Middle East or South America is instantly displayed on Pentagon computers.
- Raising awareness allows for cooperation and self-synchronization between different units and types of troops, which, in turn, dramatically increases the effectiveness of the combat mission. One of the features of the network-centric war is the possibility of self-organization at the grassroots level and horizontal links between various units on the battlefield.

Distinctive features of the network-centric war are:
- The command has the opportunity to use the armed forces, separated geographically. Previously, it was necessary that the units and their support services were located next to each other and in close proximity to the enemy or the object that is being held. Now these restrictions have been lifted, which was confirmed in the course of actual hostilities. Any war is not only a unit of soldiers going on the attack, but also the most difficult logistical task; it is especially difficult to solve it in a modern war of maneuver. Using network-centric methods promises a real revolution in the organization of targeted logistics. For example, during the operation "Iraqi Freedom" in 2003, the US armed forces for the first time used the MTS information system (Army's Movement Tracing System). With the help of a huge number of sensors, they tracked the location of tanks, armored personnel carriers and infantry fighting vehicles throughout the theater of operations and received requests for the supply of ammunition, spare parts, fuel from their crews in real time. The MTS system has cost the US taxpayers $ 418 million, its membership consisted of more than 4 thousand on-board computers and 100 servers.
- Only highly developed states with a large military budget are capable of conducting network-centric wars. Using advanced computer and information technology, the armies of such countries are able to establish comprehensive surveillance of the theater of operations. Before the start of the second war in Iraq (2003), the Americans deployed a large satellite constellation of more than forty satellites over this country.
- Creating a common information network allows you to establish effective interaction between various actors in the combat space. This creates an opportunity for divisions geographically divided to carry out joint actions, distribute tasks among themselves and the volume of work, which allows them to respond more quickly to changing situations. This feature of network-centric hostilities contributes to the self-organization of the armed forces at lower levels, the creation of horizontal links between various units. Self-organization and self-synchronization provides an opportunity for grassroots subdivisions to operate almost autonomously, independently formulate and solve operational tasks, based on access to the general information array and understanding the command plan. For example, more than 80% of aviation sorties from the beginning of 2000 (campaigns in Afghanistan and Iraq) have been carried out without prior determination of targets; they come to pilots directly from ground units at the front line. To do this, the Americans had to develop another communication and control system - TVMSS (Theater Battle Management Core Systems).
In Iraq, the squadron commanders of carrier-based aviation, using a common information system, could conduct joint planning of future operations with their army counterparts.
In addition to the principles, elements and main differences of the network-centric war, there are also the main phases of such conflicts. Initially, they were described by the theorists of this doctrine, and then confirmed in practice. There are four main phases:
- Destruction of enemy intelligence information system: intelligence equipment, headquarters, information processing and control centers.
- The conquest of full air supremacy by suppressing and destroying the enemy's air force and air defense.
- Destruction of the ground forces of the enemy, with special attention paid to missile systems, artillery and armored vehicles.
- Suppression of focal resistance of the enemy.

"Iraqi Freedom": the first postcentral network-centric war
The American operation Iraqi Freedom (2003) is considered the first network-centric war in history. Many Russian experts consider the second US war in Iraq a conventional air-to-ground war, which is, in fact, a kind of deep operation. However, if you look closely, you can see significant differences of this conflict, which directly indicate its network-centric nature.
First of all, the unusual ratio of the advancing and defending troops, as well as the surprising transience of this campaign, are striking.
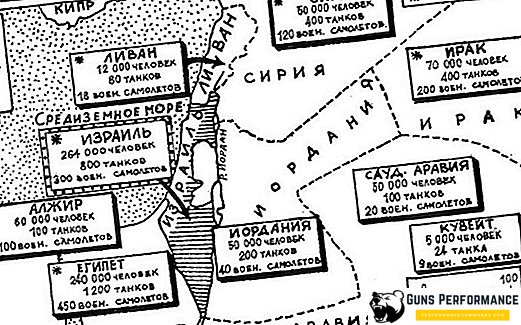
Before the invasion of the US-British coalition, the army of Iraq was a serious military force with a rich military experience, including the fight against the armed forces of Western countries. Saddam Hussein had 23 divisions of land forces and elite Republican Guard, a total of more than 230 thousand people. In addition, another 200 thousand soldiers and officers served in the air defense forces and aviation. Iraq had 2,200 tanks (of which more than 700 were T-72), more than 3 thousand infantry fighting vehicles and armored personnel carriers, 4 thousand units of barrel artillery, MLRS and mortars. At the disposal of the defending side were medium-range ballistic missiles (100 pieces), 500 combat helicopters and aircraft, more than a hundred air defense missiles of various types. In addition, Iraq had irregular troops, and the number of reservists was 650 thousand people.
The Americans, along with the British, had six land divisions (110 thousand people), 180 thousand people in aviation and in the navy, they were armed with 500 tanks, 1300 infantry fighting vehicles and armored personnel carriers, 900 barreled and rocket artillery, 200 ZRK . The main force of the Allies, of course, was aviation - the strike force could count on 1,300 helicopters and airplanes, as well as 1,100 cruise missiles.
That is, it turns out that before the outbreak of hostilities, the ground forces of the advancing side were inferior to the defenders several times (in tanks and artillery 4.4 times). Amazing situation for any operation. The coalition had an overwhelming superiority in the air, but the Iraqis were ready for this: they generally refused to use their own aircraft, knowing that it would be instantly knocked out. The ground forces were extremely dispersed and placed their defensive lines in areas with difficult terrain, hiding behind natural obstacles.

Iraqi divisions have prepared a deeply echeloned defense, based on a large number of strongholds located on the outskirts of cities. Their tactic was clear: to impose on the enemy fights on previously prepared positions and to cause him unacceptable damage. The command of the Iraqi army promised the enemy to turn Baghdad into a new Stalingrad. In the event of a breakthrough of defensive positions, the troops must retreat to the cities and start urban battles.
The strategic plan of the Allied operation consisted of several points. First of all, they had to win complete air supremacy, suppressing Iraqi air defense. Then the coalition ground forces intended to encircle the Iraqi units located around Basra, deliver a flank attack on the enemy’s first echelon of defense and, after a raid on the desert territory of the country, strike Baghdad.
The task of winning air supremacy was solved very quickly, after which the coalition aviation began to launch attacks on ground targets and support for ground forces.
One British division blocked Basra, and three American - went to the raid on Baghdad. Four days later, the Americans reached the outskirts of Baghdad, and after about two weeks the capital of Iraq was taken to the ring. All the counterattacks of the defenders were repulsed with heavy losses for them, and soon the general desertion of Iraqi soldiers began.
The defeat of the Iraqi army seems to be a typical air-ground operation, with massive use of combat aircraft, but this is not entirely true. It was only through the use of network-centric tools that the Americans managed to achieve such quick and impressive results.

Все воздушное пространство Ирака круглосуточно контролировалось с помощью самолетов AWACS, с их помощью происходило и управление авиацией коалиции. Американцами использовалась радиолокационная система J-Stars, установленная на борту самолетов. Она выявляла источники радиоизлучения противника, по которым уничтожались РЛС, станции РЭБ, ретрансляторы, радиопередатчики.
Важнейшую роль в успешном завершении американской кампании в Ираке сыграла система управления и связи FBCB2. Она связывала в единую информационную сеть системы разведки, целеуказания, позиционирования, планирования боевых действий и снабжения войск. Опытные версии FBCB2 использовались во время военных конфликтов в Афганистане и Югославии.
Терминалы системы FBCB2 были установлены на всех танках, БМП, БТР, САУ и РСЗО. Ими обеспечивались наземные командные пункты, передовые наводчики артиллерийского огня и авиации. Система FBCB2 имела двухуровневую систему связи: с воздушным и космическим сегментом.
Используя систему FBCB2, командиры низшего звена имели доступ к информации о расположении своих войск и подразделений противника, поэтому атаки на иракские позиции и опорные пункты чаще всего осуществлялись с тыла или флангов. Имея представление, где находится неприятель, американцы стремились вести огонь на дистанциях, которые исключали попадание под ответный огонь противника. С помощью FBCB2 командиры американских подразделений могли на поле боя напрямую взаимодействовать с артиллерийскими подразделениями и с авиацией.

Иракская артиллерия обнаруживалась сразу же после первых пристрелочных выстрелов с помощью радиолокационных станций. В воздухе постоянно находилась авиация коалиции, которая незамедлительно получала информацию прямо от передовых частей.
Иракцы попадали под огонь противника уже на этапе сосредоточения войск, они не могли нанести урон противнику даже ценой собственной гибели. Это сильнейшим образом деморализовало войска. Силы коалиции, полностью владея тактической информацией, наносили превентивные удары по скоплению иракских войск, уничтожали силы противника по частям.
Пользуясь подавляющим информационным преимуществом, силы коалиции могли уничтожать даже превосходящего по численности противника. Немногочисленные попытки контратак всегда разбивались о полную осведомленность войск коалиции о том, где и какими силами ожидать удара.
Сетецентрические методы ведения войны позволяли американским командирам всегда быть на несколько шагов быстрее, чем их противники. Также следует отметить тот факт, что в нанесении ударов силы коалиции отдавали приоритет штабам и узлам связи противника. После их уничтожения иракские подразделения, построенные по иерархическому принципу, превращались просто в вооруженные и неуправляемые толпы.
После окончания войны 2003 года в Персидском заливе американцы продолжили совершенствовать инструменты сетецентрической войны. В настоящее время работает программа Joint Battle Command Platform, согласно которой носимыми терминалами оснащаются все военнослужащие подразделений постоянной готовности. Система FBCB2 расширена до уровня С4. Ударными темпами происходит увеличение количества беспилотных летательных аппаратов в войсках, их количество превысило численность танков. Причем, большая часть дронов выполняет разведывательные функции.
В 2010 году было создано Кибернетическое командование, под руководство которого отдали GIG. Оно непосредственно подчиняется Стратегическому командованию страны. То есть, американцы приравняли информационную сеть к ядерной триаде.

А что Россия?
Вооруженные силы России до сих пор опираются на доктрину глубокой операции, которая была разработана в 30-е годы прошлого столетия. Основной упор делается на наращивании количества боевых платформ (самолетов, танков, ЗРК) и улучшения их качества.
Подобная стратегия выглядит ошибочной. В конфликте, когда один из его участников использует сетецентрические методы, количество танков и ЗРК отходит на второй план. Куда важнее скорость управления имеющимися силами. Конфликт двух противников, один из которых использует сетевые информационные технологии для управления войсками, напоминает бой слепого боксера со зрячим. Абсолютно неважно, насколько хорошо подготовлен слепой боец - ему все равно не победить.
В России существуют единичные разработки систем вооружения и управления, которые можно было бы использовать в сетецентрической войне, но они уже многие годы находятся в стадии испытаний, нет необходимой системы связи, отсутствуют протоколы обмена информацией между различными подразделениями и родами войск.